- DataMigration.AI
- Posts
- Kickstart Your Zero Trust Migration: A 5-Step Implementation Guide
Kickstart Your Zero Trust Migration: A 5-Step Implementation Guide
A Phased Approach to Zero Trust Adoption.
What’s in it?
80% of Zero Trust migrations fail due to poor strategy, not lack of effort.
Zero Trust is a design philosophy, not a product you install.
VPNs assume trust; attackers exploit that single foothold.
Start by defining your "protect surface", what matters most, not everything.
Map users, devices, and workflows before enforcing any controls.
Replace broad VPN access with granular, app-specific access.
Zero Trust Migration Secrets: Why 80% of Security Strategies Fail (And the Powerful Way to Fix Yours)
Organizations everywhere are buzzing about Zero Trust. Boards are giving the green light on budgets, CISOs are sketching out roadmaps, and vendors are touting their foolproof protection.
But here’s the hard truth: a lot of Zero Trust migration efforts hit a wall, fall apart, or just fade away without making a real impact.
So, what’s going wrong?
It often boils down to teams jumping straight into technology instead of laying out a solid strategy.
They grab tools, set up dashboards, and slap a “Zero Trust” label on their existing controls. Yet, attackers still find ways to move laterally, VPNs get bogged down, and access issues keep piling up.
The core problem isn’t about the effort being put in.
It’s about the lack of clear direction.
Let’s break down the issue first, and then we will outline a smarter way forward by considering the recommendations of the National Cyber Security Centre in the UK, Cloudflare’s framework on migrating networks, and the current Zero Trust migration practices to the cloud.
The Real Problem: Treating Zero Trust Like a Product
One of the biggest blunders I often come across is this: many organizations think that Zero Trust is just a software solution you can install. But that’s not the case at all.
Zero Trust is more of a design philosophy. It operates on the principle that there’s no implicit trust, whether inside or outside the network. Every single request needs to be verified, and every access must be justified.
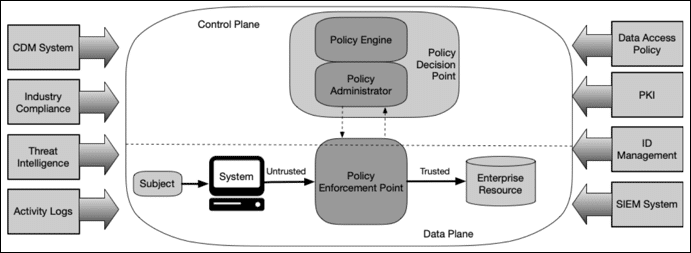
According to the UK’s NCSC guidance on Zero Trust migration, organizations shouldn’t try to overhaul everything in one go. Instead, they should adopt a gradual, risk-based approach.
But here’s where companies often miss the mark:
They try to overhaul their entire VPN setup all at once.
They enforce strict policies without really understanding the situation.
They overlook their most vital assets.
They disregard essential business workflows.
They make the architecture unnecessarily complex.
What’s the outcome? Disruption. Frustration. Drained budgets. Security teams feel the heat. Business leaders start to lose their cool.
Zero Trust turns into just another buzzword instead of a real change.

Why VPN-Centric Security Is Breaking Down
Traditional VPN models have always assumed that once a user is “inside” the network, they can navigate freely. This was effective when workforces were centralized, and applications were hosted on-site.
But what about today?
Cloud workloads are now the norm. Remote work is standard practice. SaaS platforms are everywhere you look.
Cloudflare’s guide on network and VPN migration highlights an important reality: centralized VPN architectures can create bottlenecks, increase attack surfaces, and negatively impact user experience.
VPN concentrators can result in:
Performance bottlenecks
Broad internal access
Opportunities for lateral movement
Limitations in scaling
In today’s threat landscape, this model is quite fragile. Attackers don’t need to breach everything; they just need a single foothold.
The Smarter Start: Define Your Protect Surface
The NCSC wants you to know that when you begin your Zero Trust journey, you should first define what you are protecting. By what, they mean what matters most to you, not everything.

You should define a protected surface that you will protect. This protective surface may be:
Sensitive data stores
Financial resources
Identity infrastructure
Mission-critical apps
The difference here is that rather than protecting the whole edge of the network, Zero Trust focuses narrowly and precisely on what matters most.
This changes everything.
When you define what matters most to you by defining what you are protecting, you can begin to create security around those areas. Security becomes a strategic and proactive effort rather than a reactive one.
The shift from reactive to proactive security starts with a simple question: What are we really protecting?
Once you define your sensitive data stores and mission-critical apps, you need a way to see them, govern them, and control access across a sprawling, decentralized landscape.
DataManagement.AI provides the end-to-end lineage and always-on security to protect what matters most because you can't secure what you can't see.

Step One: Map Business Processes Before Enforcing Controls
Before rolling out your tools, take a moment to consider the following:
Who is using what?
Where are they using it from?
What device are they using it on?
What are they really trying to accomplish?
The Trigyn Zero Trust cloud migration framework does not focus on rules; it focuses on synchronizing with your business needs. Security should enhance your business, not impede it. When you know your business, your rules will only enhance productivity.

You will also realize your hidden dependencies along the way.
Most organizations overlook this very important step in the process. They implement access controls without a second thought, only to increase help desk calls and annoy their executives.
Take your time with this step.
Visibility first, then enforcement.
Step Two: Strengthen Identity as the Core Control
At the center of all this is identity.
If you can’t verify who someone is, then everything else starts to fall apart.
As you move forward to a modern Zero Trust architecture, you’ll generally add:
Multi-factor authentication
Centralized identity management
Conditional access
Least privilege
Continuous authentication

But there’s a catch: identity isn’t just about people.
It’s also devices, applications, APIs, and services. And these entities need to verify their legitimacy to access what they need. A well-defined identity model helps to remove dependence on network location as a measure of trust.
Step Three: Replace Broad VPN Access with Granular Access Controls

This is where the real difference starts to show up.
Rather than providing users with access to the network as a whole via a VPN, Zero Trust only grants access to specific applications.
Cloudflare's migration process creates a plan to transition the network in a step-by-step fashion:
Identify the internal applications users are currently accessing via a VPN.
Segment access based on user role.
Replace network access with access to specific applications.
Remove any exposed areas of the network not in use.
And the outcome?
Users are only accessing exactly what they need, and nothing more.
That's a huge reduction in the risk of lateral movement.
Step Four: Implement Least Privilege Gradually

Least privilege sounds like a simple concept.
But in old systems that have been around a while, users have developed privileges that have accrued over time.
Removing them in one go can be risky.
So it’s a complex process that requires:
Auditing existing permissions
Closing inactive accounts
Reducing admin privileges
Monitoring actual usage
Phasing in changes
Moving to Zero Trust is an evolution, not a revolution.
Step Five: Apply Segmentation Intelligently
Microsegmentation: this helps to keep systems separate and tightens the isolation where it counts.
But be careful not to overdo it, or you risk destabilizing the environment.
First, tackle the high-risk areas:
Financial systems
Customer databases
Production workloads

Then, gradually move from there. Secure the most critical assets of the organization first.
Common Zero Trust Migration Mistakes to Avoid
Cut to the chase. These are the mistakes that are derailing programs:
Trying to change the entire network at once
Not understanding the dependencies of the existing systems
Investing in tools without fully understanding the risk
Not including business leadership in the conversation
Thinking of Zero Trust as a single, one-time project
Zero Trust is not a single, one-time effort. It's a continuous process. Threats evolve, infrastructure evolves, and policies have to evolve as well.
Measuring Real Zero Trust Success
Don’t measure your success based on the sheer number of tools you deploy.
Concentrate instead on the end result:
Less privileged accounts
Better authentication coverage
Shorter paths of lateral movement
Faster detection of anomalies
Better user experience
Is productivity up while risk is down? You’re winning. Is productivity down while risk is up? Take a step back.
Zero Trust and Cloud Migration: Why They Must Align
Zero Trust thrives when embedded within cloud transformation from the outset, not tacked on afterwards.
With cloud-native architectures, the benefits include:
Dynamic policy enforcement
API-based access control
Real-time telemetry
Scalable identity services
However, mismanaged cloud environments can lead to shadow access issues.
This is exactly where intelligent data governance comes in.
Transform Your Zero Trust Strategy
The success of Zero Trust migrations is based on visibility, especially in the area of data.
How can you possibly ensure a successful Zero Trust migration if you don’t know where your sensitive data resides, how it moves, and who it interacts with? Well, the answer is simple: you can’t, and that is a risk you shouldn’t want to take.
At Datamanagement AI, we are here to illuminate your complex data world. We use our AI-based platform to not only find your sensitive data, data dependencies, and governance, but also ensure your Zero Trust migration is based on actual data, not assumptions.
Want to know how it works?

The Real Answer: Where Should You Start?
Zero Trust projects fail when they're based on the pursuit of perfection. They succeed when they're based on achieving simple clarity of outcome. Start with what you're protecting in the first place. Secure who you're allowing to have access to it.

Shift away from the broad permissions of VPNs to specific, granular permissions. Apply the principle of least privilege with care. Segment with intelligence. Make security work with the business, not against it. That's where the real power of Zero Trust comes from.
Zero Trust is not about distrust; it's about verification. When done well, it's not just about protecting an organization from harm but allowing it to thrive. The question is not "Do we need Zero Trust?" but "Are we prepared to do it correctly?"
Thank you for reading
DataMigration.AI & Team